Doppelgänging and Digital Forensic Analysis
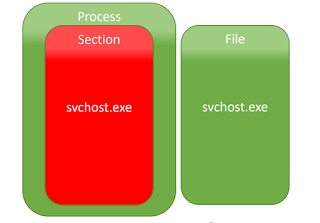
Read Time: 10 Minutes Recently, Catalin Cimpanu released a article about a new Process Hollowing Technique named Doppelgänging. The highlights of the article include undocumented features of the Microsoft Windows operating system, antivirus inability to scan NTFS transactions, and "...cannot be patched since it exploits fundamental features and the core design of the process loading mechanism in Windows". The article further discloses that BlackHat EU would be releasing the presentation. So I found the powerpoint of the presentation, titled Lost in Transaction: Process Doppelgänging , which reveals the API Calls and some interesting assertions by the researchers. You can find additional information about NTFS Transactions on Microsoft Developer Network (MSDN) shows some basic information regarding the API Calls referenced in the presentation. The sequence of API calls according to the presentation is as follows: Create a transaction Open a "clean&qu