Doppelgänging and Digital Forensic Analysis - Part Deux
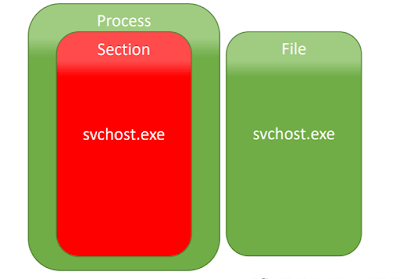
Read Time: 15 Minutes On 17th of December 2017, I wrote a blog post reacting to Blackhat 2017 EU presentation on a new Process Hollowing Technique named Doppelgänging . The original presentation from Blackhat (BH) EU 2017 can now be found on youtube to be seen it's full glory. At the time I did not have proof of concept (POC) code and just a day later Hasherzade wrote some POC code / blogged about it. Figure 1: Doppelgänging Conceptual Model Leveraging his code I took a stab to see what I could find based on the observations I made in my blog post and leveraging current memory analysis techniques to see what other indicators I could spot. From my blog post I cited references from the original presentation, at BH EU 2017, that included looking at the windows executive object "FILE_OBJECT" and the attribute "ImageFilePointer". Also, I remarked that the NTFS $LogFile would give some valuable clues. Looking at the "FILE_OBJECT" for t

