VBN File Analysis - Decrypting for the Masses
Read Time: 5 Minutes
In 2012, Hexacorn Ltd posted a couple blogs on their website about decrypting VBN files: the original post and a second post. The team at Hexacorn Ltd identified that "...Symantec’s VBN files can be encrypted not only with 0x5A, but also 0xA5..." in their original research. In their later posting disclosing that the encrypted is separated by a "...5 byte ‘chunk divider’ in a form of 0xF6 0x?? 0x?? 0xFF 0xFF. So, to reconstruct the encrypted Quarantine files, one needs to decrypt them with 0xA5 first and then remove the chunk dividers...". Which are both valuable insights that I can confirm should be observed in the decryption of VBN files.
For 2018, here are a few more insights into the data structures and analysis considerations for decrypting VBN files:
In 2012, Hexacorn Ltd posted a couple blogs on their website about decrypting VBN files: the original post and a second post. The team at Hexacorn Ltd identified that "...Symantec’s VBN files can be encrypted not only with 0x5A, but also 0xA5..." in their original research. In their later posting disclosing that the encrypted is separated by a "...5 byte ‘chunk divider’ in a form of 0xF6 0x?? 0x?? 0xFF 0xFF. So, to reconstruct the encrypted Quarantine files, one needs to decrypt them with 0xA5 first and then remove the chunk dividers...". Which are both valuable insights that I can confirm should be observed in the decryption of VBN files.
For 2018, here are a few more insights into the data structures and analysis considerations for decrypting VBN files:
- The first 388 bytes is reserved for the original directory and filename of the quarantined file
- The next 2052 bytes contains meta data regarding the detection to include: hostname of the system, username associated at the time of the detection, signature name, the directory/filename, and more.
- The next 516 bytes is "To Be Determined" with respect to what is hosted here
- The next 1796 bytes contains the location the VBN file is original from and other proprietary data.
- The next section of data is "0x5A" XOR encrypted. This section appears to end at the encrypted header of MZ which is "0xE8 0xFF". This section appears to repeat the information disclosed in clear text from the prior sections above.
- The rest of the data that follows is decrypted with "0xA5" starting with "0xE8 0xFF". This is the original file with the chunk dividers.
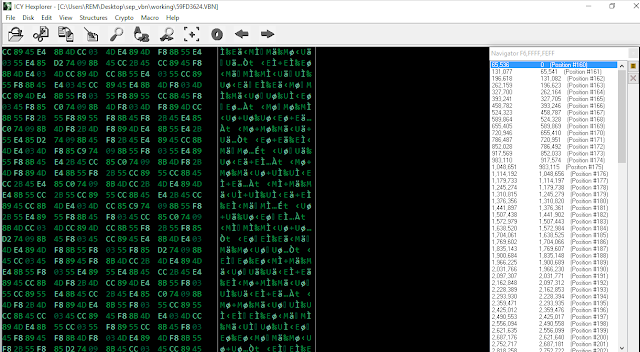
At this point if you extract the original file with the chunk dividers and look for occurrences of "0xF6". The first occurrence of interest should be between at 65.4k and 65.7k byte offset. The 5 byte stream you are searching for is "0xF6 0x?? 0x?? 0x?? 0xFF". If you find a 5 byte stream that meets this criteria search for all instances. (See Figure 1 - Finding Chunk Dividers) If those instances are 65.4k thru 65.7k apart then the right divider has been found. All of these need to be removed to restore the original file.
Please leave comments below and I look forward to sharing more experiences that I have on the daily with my readership.
References
Figure 1 - Finding Chunk Dividers (See Reference #3)
Please leave comments below and I look forward to sharing more experiences that I have on the daily with my readership.
References
- Hexacorn. Tech Blog. "Update" http://www.hexacorn.com/blog/2012/04/15/update/
- Hexacorn. Tech Blog. "DeXRAY – Decrypting VBN files, Part 2" Article http://www.hexacorn.com/blog/2012/09/21/dexray-decrypting-vbn-files-part-2/
- Hexplorer Tool. https://sourceforge.net/projects/hexplorer/files/hexplorer/

Comments
Post a Comment